Analysis of abnormal detection methods for central control gateway instructions
- author:
- 2024-06-06 09:10:58
As industrial control systems continue to evolve and become more complex, cybersecurity issues have gradually become prominent. As a key component of the intelligent control system, the central control gateway shoulders important responsibilities such as protocol conversion, data exchange and security protection. However, in view of the loopholes and flaws in the command control mechanism of the central control gateway, it may be exploited by malicious attackers, which may cause abnormalities or even paralysis of the system. Therefore, it is necessary to design an efficient anomaly detection plan to detect and block abnormal command control behaviors in a timely manner.
system architecture design
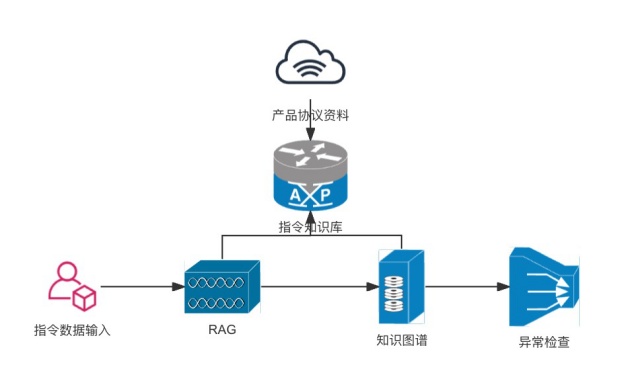
This paper proposes a central control gateway command control anomaly detection plan that combines Retrieval Augmented Generation (RAG) and knowledge graph technology. This solution uses the RAG model to retrieve relevant knowledge from the product instruction library, and combines the reasoning capabilities of the knowledge map to carry out semantic analysis and anomaly detection on the instruction control behavior.
system architecture design
The system architecture of this anomaly detection plan consists of the following main modules:
- input module
从中控网关获取指令控制数据,包含指令内容、协议类型、受控端设备等信息。
- Product instruction library module
依据智能控制系统的标准规范与最佳实践,构建涵盖指令控制知识的产品指令库。Product instructions store protocol instructions, operating attributes, connection relationships, etc. of gateway and terminal equipment in a structured form in a library.
- Knowledge Map Module
将产品指令库中的知识转化为知识图谱表示,建立实体、关系和属性之间的语义联系。Connect the attributes of the gateway operation port and the attributes of the terminal receiving port through the relationships of input, output, prohibition, and connectivity to build a knowledge graph between the gateway and multi-device terminals.
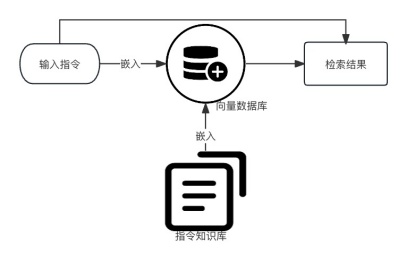
- anomaly detection module
将 RAG 模型整合的指令操作图与知识图谱进行语义匹配,利用图谱推理能力判断生成的指令操作图行为是否异常。
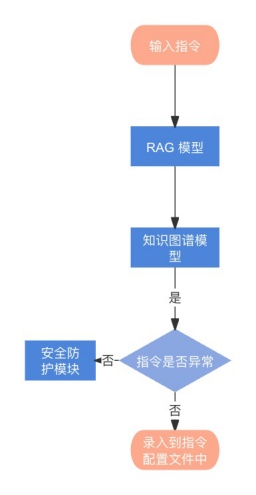
realization flow
- Data input: Obtain command control data from the central control gateway and encapsulate it into json data containing command content, protocol type, controlled end equipment and other information.
- Construction of product instruction base: Integrate equipment instructions, protocol types, product numbers, data link roles and other information of all controlled terminals into the product instruction base of the central control gateway for storage.
- Knowledge graph construction: Convert data in the product instruction base into knowledge graph representation. First, the data is labeled with entity classes. In the command knowledge base, the specific product equipment and the central control gateway are entities. Then the entities are associated to the knowledge graph, and entity corresponding information is obtained through the association relationship and the knowledge graph; secondly, conceptualization is carried out, and based on the current context, dynamically identify the roles of the product equipment in the entire data chain; finally, understand the relationships between entities and establish semantic connections between entities, relationships and attributes.
- RAG model: First, data is encoded from the instruction knowledge base to generate embedded vector blocks, and then the blocks are stored in the vector database to build a data index. Then, the input instruction data is converted into a searchable data structure, so that it can retrieve relevant text data from the vector database based on vector similarity, use these retrieved information to guide, and generate output results based on the retrieval results and the input instructions.
- Abnormal detection:
将输入的指令控制数据输入到 RAG 模型中进行嵌入向量后输入到 RAG 模型的检索模块中,并从向量数据库中查找与输入指令相似度高的相关知识信息。The generation module of the RAG model generates output results from the retrieved knowledge information and input instruction data. Finally, the output results of the RAG model are used in the knowledge graph to identify and compare the semantic similarity or correlation of entities, relationships and attribute values, and the graph's logical reasoning capabilities are used to judge whether the input command manipulation is reasonable or abnormal. If an abnormality is detected, corresponding security measures are triggered.
- Model optimization: Continuously optimize RAG models and knowledge maps based on actual operation conditions to improve the accuracy and efficiency of anomaly detection.
This anomaly detection scheme combines two advanced technologies: RAG and knowledge mapping, and can effectively detect the command control abnormal behavior of the central control gateway.
该异常检测方案融合了 RAG 和知识图谱这两种先进技术,能够有效检测中控网关的指令控制异常行为。By building a product instruction base and knowledge graph, the RAG model can retrieve relevant information from massive knowledge and combine semantic reasoning capabilities for anomaly detection. This solution has strong scalability and adaptability, and can be applied to different types of industrial control systems. In the future, we will further optimize the performance and robustness of this solution to better ensure the safety of industrial control systems.
TAG: